Which of the Following Best Describes Detective Controls
BB Critical Thinking Accessibility. Technical is a class of control.

Preventative Control An Overview Sciencedirect Topics
5 states that internal controls may be preventive or detective.
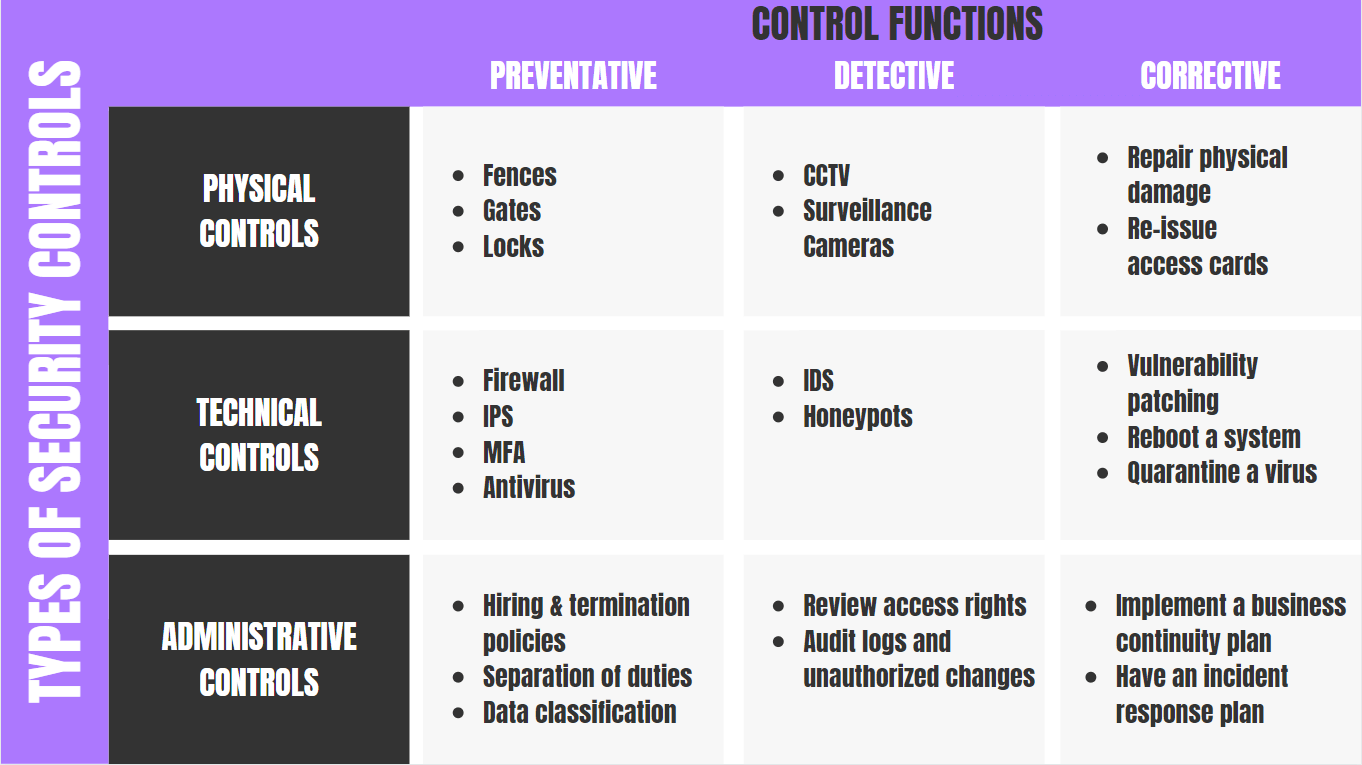
. Integrated auditing places internal control in the hands of management and reduces the time between the audit and the time of reporting. Detective controls are designed to detect a threat event once that event has occurred. Reduce the effect of an attack.
Which of the following controls is preventive. 04-02 Identify the. Examples of detective controls include the following.
Integrated auditing combines the operational audit function the financial audit function and the IS audit function. Detective controls are designed to detect a threat event once that event has occurred. Multiple Choice O Management periodically determines whether the amount of physical assets agree with the accounting records The company should establish formal guidelines to handle cash receipts and make purchases Important documents should be kept in a safe place and electronic files.
A preventive control prevents the event from occurring. Requiring two persons to open mail containing payments. Physical access controls B.
Which of the following is primarily a detective control in the Remote Access Domain. Detective controls aim to reduce the impact of such events. A corrective control takes action to reverse the effects or impact of an incident.
The employment of trustworthy people to enter data into the information system. Which of the following is an example of a detective control in an information system. Access-control software that uses passwords tokens andor biometrics B.
Internal audits and other reviews. Discover attack and trigger preventive or corrective controls. In which situation would a detective control be warranted.
Examples of detective controls include the following. Reduce the likelihood of a deliberate attack. So the detective control detects the transposition error in the book.
Detective control may be employed in accordance with many different goals such as. Which of the following is the best example of a detective control. It is designed to test the skills and knowledge presented in the course.
Which of the following is not one of the four common elements needed to determine whether fraud is present. 2 Medium Learning Objective. Backup procedures used to archive data D.
This quiz covers all of the content in Cybersecurity Essentials 11. While corrective controls keep errors from resulting in loss B detective controls do not warn deterrent controls do. Which of the following is an example of detective controls.
A type of internal control mechanism intended to find problems within a companys processes. Ensure the organization hires the right people. Echo controls in telecommunications.
Audit trails capture information which can be used for detecting errors. Checkpoints in production jobs. There are multiple task types that may be available in this quiz.
Quizzes allow for partial credit scoring on. The bank reconciliation statement is a part of the accounting process. 41 Which of the following best describes detective controls.
An audit log is a detective control because it identifies events either as they are occurring or after theyve occurred. Audit trails The correct answer is. The PCAOBs AS No.
Which of the following best describes the purpose of personnel policies and procedures. Detective corrective monitoring logging recovery classification and directive. Automated reports to management that specifically identify delinquent receivables.
Therefore they are considered to be detective controls. While both are after the fact A the order of application is not really relevant. Checkpoints in production jobs.
Detective controls aim to reduce the impact of such events. Which of the following best describes the approaches that should be put into place if an organization wants to integrate a way to improve its security processes over a period of time. Segregation of duties C.
A threat model can help to assess the probability the potential harm and the priority of attacks and thus. Which of the following best describes what this model is and what it would be used for. Assurance from top management that computer centers are kept locked.
Internal audits and other reviews. Echo controls in telecommunications. Detective control The detective control is a part of the internal control where it assists to detect the errors in the accounting book.
Which of the following best describes integrated auditing. Dual control which is an administrative detective control that can ensure that two employees must carry out a task simultaneously. AnswerD The correct answer is D.
THIS SET IS OFTEN IN FOLDERS WITH. Dual control is an. Which of the following are good examples of strings integers and decimals.
Which statement best describes a motivation of hacktivists. Which of the following best describes common body of knowledge. What are the seven main categories of access control.
Employee management is the activity of preventive controls that provides the employees with proper and accurate knowledge that they need to perform their jobs or duties.

The 3 Types Of Security Controls Expert Explains

This Deep Quiz Will Determine Who You Really Are In Less Than 20 Questions Quizzes

Comments
Post a Comment